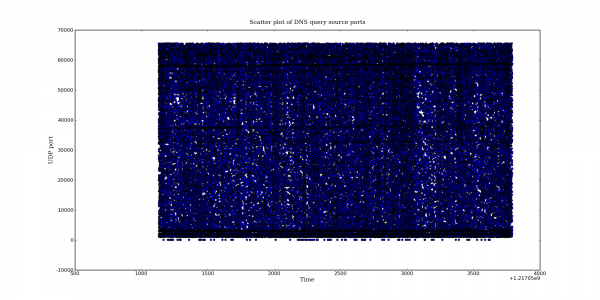
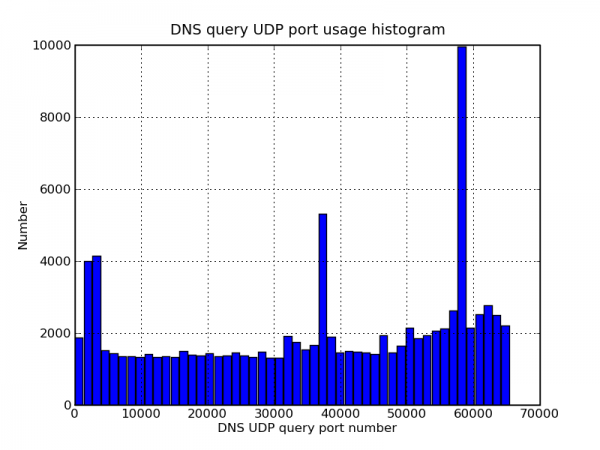
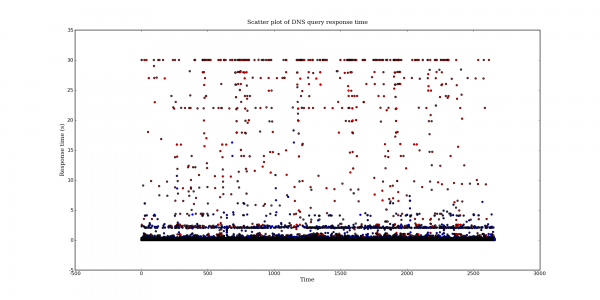
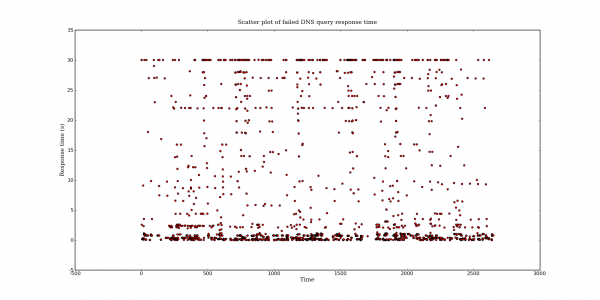
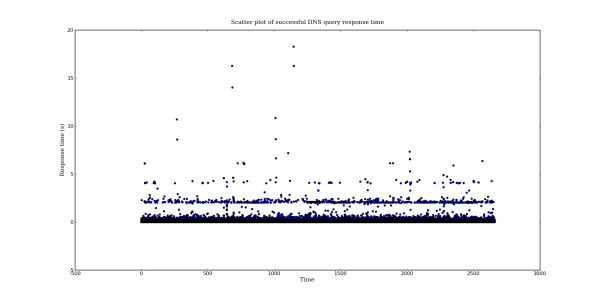
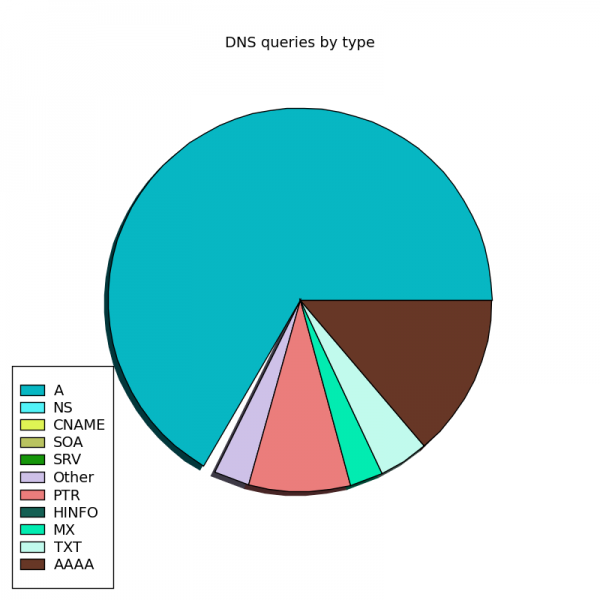
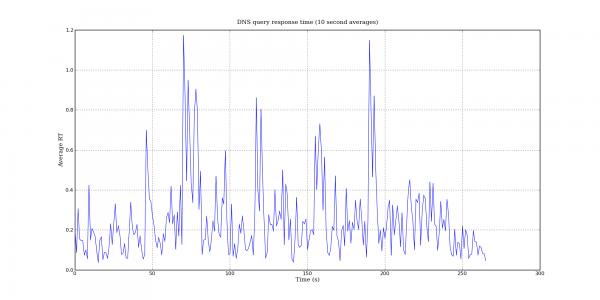
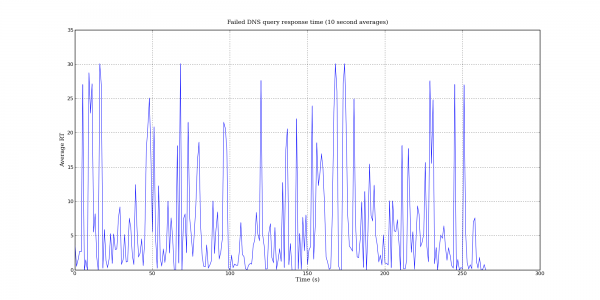
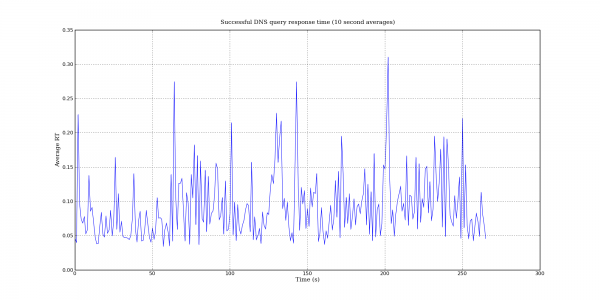
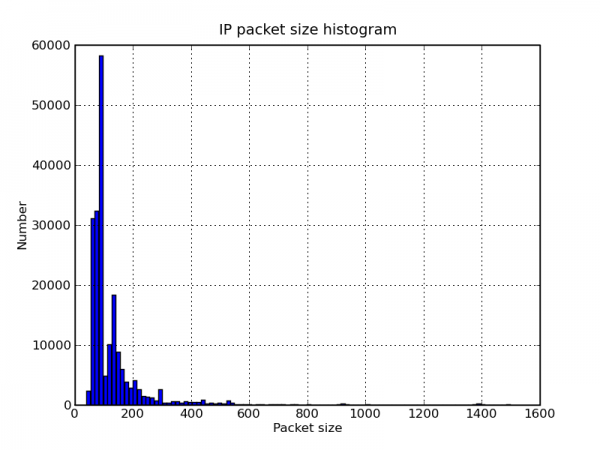
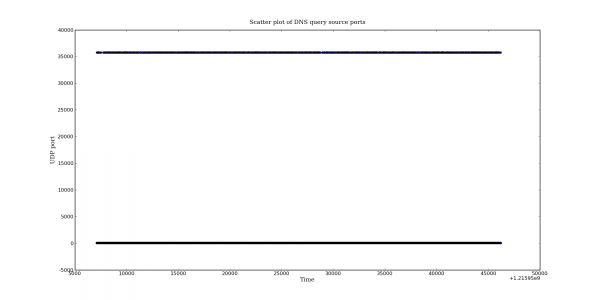
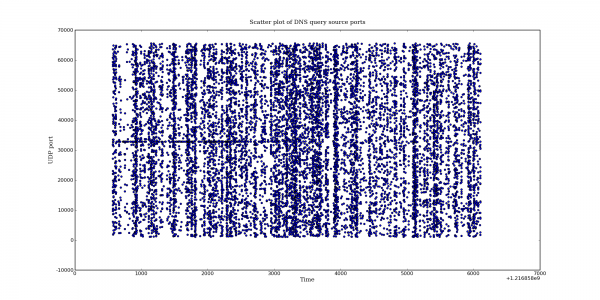
Following my last post on DNS query port usage, here are some more interesting DNS graphs.
The following graphs are based on a packet capture taken from the network interface of a recursive DNS server. This DNS server is one of the primary recursive DNS servers for a small Internet service provider. The capture includes all UDP DNS traffic to the DNS server as well as UDP DNS traffic from the DNS server to addresses within the local AS.
/usr/sbin/capinfos local.pcap File name: local.pcap File type: Wireshark/tcpdump/... - libpcap File encapsulation: Ethernet Number of packets: 200000 File size: 30702100 bytes Data size: 27502076 bytes Capture duration: 2659.328827 seconds Start time: Sat Jul 26 01:45:31 2008 End time: Sat Jul 26 02:29:50 2008 Data rate: 10341.74 bytes/s Data rate: 82733.89 bits/s Average packet size: 137.51 bytes